I was recently made aware of Kodachi Linux, which according to it’s website has gotten critical acclaim. This is a superficial attemt to look at the distribution – if it’s even fair to call it that.
Off the bat, it doesn’t start well:
Confusing documentation
For best security results (Email – Banking – Cryptocurrency):
- ISP > Host machine (XMR anonymous VPN) > Linux Kodachi VPN (Virtual machine – Vmware) with firewall forced VPN Traffic > Kodachi browser > Dnscrypt (Best model)
- ISP > Linux Kodachi VPN with firewall forced VPN Traffic > Kodachi loaded browser > Dnscrypt
- ISP > Linux Kodachi VPN with firewall forced VPN Traffic > Kodachi loaded browser > TOR DNS
- ISP > Linux Kodachi VPN with firewall forced VPN Traffic > Kodachi lite browser > TOR DNS (Fast)
- ISP > Linux Kodachi VPN with firewall forced VPN Traffic > TOR browser > Dnscrypt
- ISP > Linux Kodachi VPN with firewall forced VPN Traffic > TOR browser > TOR DNS
This confuses security and anonymity. While the majority of such sites today employ TLS (https), sending traffic through unknown VPN’s and Tor may potentially send your traffic to an attacker. You have no knowledge of the motivations of people running tor exit relays, and while they may provide anonymity, they are not meant to provide security.
Furthermore, Warith Al Maawali, the author of Kodachi, openly admits to transferring a hardware hash by default, upon boot:
I pay monthly rent to run the VPS nodes and utilize them for VPN which is provided to you, I do not collect ANY data or store ANY information (Logs) that belongs to the user except the hardware ID (hash) and connected IP address (VPN IP) that has to be sent automatically when your PC establishes a connection to the VPN
How on earth did he conclude that it was a good idea to transmit a hardware hash on boot, for a security and anonymity focused distribution? I could accept it, if it only occurred after the user choosing to use his VPN. As it is, it automatically transmits it upon boot.
What is Kodachi
Kodachi is not what I’d call a distro. The repositories are simply the default Ubuntu repositories. It’s simply Ubuntu – with a theme and some shell scripts to manage the extra security features. This should be acknowledged more prominently in my opinion, especially given the somewhat dubious license he publishes. His code is not the OS; it’s a few shell scripts.
Networking disaster
For IPv4, Kodachi at least manages to configure things correctly. A tracepath -4 vg.no indicates that yes, it does indeed go through VPN and possibly Tor:
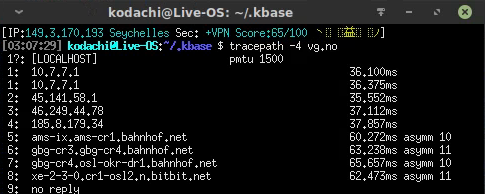
But for IPv6 it falls apart! IPv6 is enabled and functions. Note that I redacted first two hops as they’re inside my own network – but the third hop is the Hurricane Electric termination point for my IPv6 tunnel…
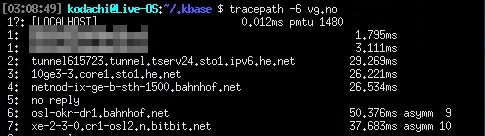
This is a devastating fault in a distribution attempting to provide anonymity! Unaware users may be trivially trackable through IPv6 – beliving the system uses the VPN’s they told it to use. Some packages that are included, such as youtube-dl will happily use IPv6 where available.
While I’m usually speaking warmly in favour of IPv6, at this point in time it probably makes more sense to just disable it totally, if your goal is anonymity. It’s a risk in this scenario, because the tools that work on IPv4 often is unaware of IPv6.
Furthermore, he seems to confuse dnscrypt and VPN. The desktop shows ISP->VPN->DNScrypt – which is… unclear. DNSCrypt is for ensuring DNS lookups, not network traffic in general!
Installed software
This section can be described as everything including the kitchen sink. It includes:
- Audacity
- Remmina
- LibreOffice
- OpenSSH server
- GCC
- Postfix (which is even enabled and listening!)
- And much, much more.
This probably stems from the fact that this is a Ubuntu Live Image, with minimal modifications. But more software means a bigger attack surface. That’s probably not a good thing in a system focused on maintaining anonymity. Software such as popularity-contest is installed, although disabled. There’s no sane reason for this being installed!
Heck, even avahi is installed. Why would you want a piece of software made for announcing your presence on such an installation anyway? It simply doesn’t make sense. Removing it would make the system work as fine, and remove one potential problem.
This is the general problem here; everything is installed, and available. This allows the user to make mistakes without realizing their mistakes. Limiting options reduces the likelihood of such mistakes, and reduces the attack surface.
File encryption
File encryption appears to be provided by a custom Python 2.x script named lock.py, with a shell script wrapper named lock. lock.py appears to be a Python script written by Joe Linoff, although the creator of Kodachi gives zero references to using this piece of software, nor that he is not the creator. The script is released under a MIT License from what I could find. As far as I can tell, Warith Al Maawali, the creator of Kodachi, does not include this license – thus not abiding by the terms of distribution for lock.py.
This is likely the reason why he writes the following in his changelog:
I tried to move to Ubuntu 20.04 but Python deprecation was a hassle for me to continue so I continued with 18.04.6 for now bare in mind that 18.04 support is still valid for Ubuntu and it should reach end of life by April 2023.
This changelog is by the way worth reading. It contains a few WTF’s.
The bash scripts
The software that actually is Kodachi appears to be a collection of bash scripts in ~/.kbase/. The quality of these scripts makes me wonder. Some of the scripts contains a bash tutorial in the top of the scripts: 
Let me show the snippet that generates the hardware hash:
function getID()
{
a=$(sudo dmidecode -s system-uuid);
b=$(sudo dmidecode -s system-serial-number);
c=$(sudo dmidecode |grep -w ID:|head -n1);
d=$a.$b.$c;
f=$(md5sum <<<$d| tr -d -|tr -d ' ');
g=$(echo $f | cut -d ' ' -f 1);
e=$g;
writeToJason "$e" "kodachihwid";
}
First of all, this is unforgivable. This is data that uniquely identifies a computer, and he transmits that. If the computer is used for anonymity, this hash allows anyone controlling the end point to check if a user corresponds to a physical computer. And Al Maawali transmits this to his own server! Stay away from Kodachi, except as a exercise of how to not do things!
Second, this snippet indicates someone who doesn’t entirely know what they’re doing, with constructs such as g=[...], followed by e=$g for no obvious reason. The poor variable naming makes mistakes more likely, and reduces readability, which is important in security related software.
But the flipside is also that it doesn’t do what the author believes it does; it’s trivial to edit the script and replace this function with the following, which will return a random, unique hash each time, thereby removing his ability to block people:
function getID()
{
writeToJason echo "$(head -n 1 /dev/urandom | md5sum | cut -d " " -f 1)" "kodachiwid"
}
It gets even better. Let’s look at how he handles networking:
IP=$(cat $Jason_web_file_name| jq -r '.ServerFeed6[].Netcheckdomain1'|xargs);
# Validate jsons here
if [[ ! -n "$IP" ]]
then
netIP="mail.com";
print_error "Failed to get json variable IP setting it to: $IP";
fi
echo "Switching domain to $IP";
echo "Dhcclient the smart way";
for i in $( nmcli device status | awk '{print $1}' );
do
if [[ $i != "DEVICE" ]]
then
echo "Dhcp for:$i";
sudo timeout 60 sudo dhclient $i;
fi
done
fi
First of all, the messages printed doesn’t make sense. Switching domain to $IP? And no, dhclient ain’t the smart way. The system uses NetworkManager. He ignores this, and runs dhclient directly. In addition, he runs it for every interface. Including lo, the loopback interface. And for good measure, he uses sudo timeout 60 sudo[...]? Why the double sudo?
This in fact leads me to the fact that this distro has enabled passwordless sudo for the default user. Why? This reduces security in my opinion. Sure, it’s more convenient, but in a security and privacy focused distribution, the author should not make such choices for the user – and the author should not make the system depend on passwordless sudo.
In addition, there’s blatant abuse of sudo where it’s clearly not needed. There’s lines such as VPN_IP=$(sudo curl -s -m 30 $randomdomain ), where sudo serves no purpose. Is the author simply used to slapping on sudo in front of commands to make sure they work, without understanding what sudo does…?
The ban function…
So he can ban users using his VPN if he considers them abusive. How does he accomplish that? Surely it has to be server side, right?
Nope. Just kidding! It’s handled client side.
function banAction()
{
SERVICE='openvpn';
if (ps ax | grep -v grep | grep $SERVICE > /dev/null)
then
sudo killall -SIGINT openvpn;
fi
SERVICE='tor-service';
if (ps ax | grep -v grep | grep $SERVICE > /dev/null)
then
sudo killall tor;
fi
So… he sends the HWID to the server, and if the server replies banned, the client politely kills all VPN connections. But it’s a bash script; it’s not exactly hard to comment out a few lines here and there.
This is a illustration of the level of brokenness in Al Maalawi’s security thinking – he doesn’t understand that you can’t trust the client in such a scenario. Would you seriously trust this guy to handle your security?
Utter lack of firewall!
One of the biggest problems is that there’s no firewall configured. Nil, zip, nada. Heck, it has postfix installed and listening!
$ nc 10.0.3.153 25
220 Live-OS.localdomain ESMTP Postfix (Ubuntu)
500 5.5.2 Error: bad syntax
This is from a different computer on the same subnet. What possible rationale does this decision have? It’s a security risk. There’s no meaningful scenario where this is wanted on a computer used to anonymously connect to the Internet. It’s only ever relevant on an e-mail server.
In addition, Kodachi doesn’t block traffic before the VPN services is up. It should! A firewall dropping incoming packages would also increase safety in case something listens by mistake – think defense in depth. A configured firewall would mitigate the by-default listening Postfix – although I’d expect the author to have better control over configured services than he shows.
The security score
Kodachi gives you a 0-100 score, supposedly to inform you how secure you are. The problem is, of course, that it doesn’t really tell you anything! Consider the following:
SERVICE='tor-service';
if (ps ax | grep -v grep | grep $SERVICE > /dev/null)
then
theModel="ISP->VPN->Tor";
securityScore=$((securityScore+30))
Kodachi doesn’t test if tor is actually in use; it’s enough that it’s running. Or how about firewall?
if(sudo ufw status |grep tun0 > /dev/null)
then
securityScore=$((securityScore+2));
fi
Too bad if the interface gets renamed to tun1. It also doesn’t check if the rules is sensible; just that some rule contains tun0 somewhere. A allow any from any with tun0 as comment will bump the score.
As it is, this number is largely meaningless. A secure system can score 0, and a secure system can score 100. At the best it’s not useful. At the worst, it’s actively harmful because a user may be mislead by a good score.
Apparmour
As it’s based off Ubuntu, Kodachi comes with Apparmour. Sadly, it only uses the default profile available in Ubuntu, with no adaptations. Apparmour could be a valuable piece of Defense in Depth, ensuring that a problem in a browser can’t compromise the entire system, by e.g. restricting the browser to read and write to a defined set of directories. This is, sadly, not done.
Discord is the point of contact.
The guy hangs out in a discord chat. The more privacy conscious people I know won’t touch discord with a 10 feet pole. Not having a IRC channel seems like a strange choice – although it doesn’t affect the security of the distribution, it’s indicative of the mindset of the author. In addition, it’s obviously a single author, not a community or group of people.
Summary
This is what I found in a couple of hours of looking. Some of the findings are serious, some merely indicate carelessness from the creator of the system – indicating that he doesn’t have good knowledge in security. The bash scripts indicates someone who has no programming background, and no Linux administration background, with strange constructs such as using NetworkManager to fetch a list of devices – but does not use NetworkManager to configure them, calls dhclient for loopback interface, and so forth.
Many of the choices won’t affect a security conscious user, but they will allow a novice to configure the system in a insecure state. More choices available essentially means that people can make more mistakes. Tails has recognized this, and provides a secure baseline, that’s not easy to break apart. Where tails allows for insecure configuration, the documentation clearly warns about this. The documentation for Kodachi is severely lacking, both in content and in warnings.
I could probably find more problems if I spend more time looking, but it’s simply not worth it. What I’ve found removes all trust in the author, and the advice is simply to stay far, far away from this piece of software. It’s not secure, and the author doesn’t know how to secure a system.
In short: Do not use Kodachi. There’s other that’s better:
They differ somewhat in scope and functionality. Read the documentation, and find the one that suits you. All of them have active communities. But stay away from Kodachi.
thank You
Thank you so much for all the important info you provided on this review, would not mind receiving up dates on software reviews.
Thanks for this review, it’s very helpful and there are not many out there on this OS.
As you pointed out this is just one guy doing this and for what it is he has put a lot of effort in, I would like to suggest you help him to try to make it better by pointing out what needs to be fixed instead of just writing it off and telling people not to use it. After all the more of these types of OS’s we have, the more people will make the switch.
I have used all the alternatives you listed above and did not like any of them, for people who are not very knowledgeable about these things kodachi has the best feel. I think kodachi is aimed at these people with little knowledge but who want privacy and security, it is a pity he did not get it right.
My point is try to help him or even do your own to cater for these people. 🙂
Oh, believe me. I attempted to hilight it to the creator. It was hand-waved away as irrelevant.
I’m new to Linux and was so happy to learn open source is superior because trillions of software genesis go over every line of code. Apparently you are the only one who spent a few hours inspecting this shitware. It is still in most top 10 lists for best privacy and security distros. Many times at number 1.
You have proven your accusations by siting clear examples. The end of Al Maawali “LICENSE” implies he is in bed with the NSA. A retired coder who is losing his faculties and was hired on the cheap by government “want-a-be’s” who are clueless to his incompetence. Yet he managed to send client info to his server where he can disapprove of content??? Who is really putting the breaks on the kiddie porn? Who would do that as they explore not so anonymous content?
Never attribute to malice what can be sufficiently explained by incompetence.
I have no reason to suspect that Al Maawali is working for anyone or receiving money for this. However, he has demonstrated incompetence in his replies.
This is very, very insightful, I appreciate it! As someone who almost fell into the Kodachi trap. I had a feeling it was too good to be true. For something to be around as long as it has and not have a lot of stellar reviews through a deep dive lens like this, it raised a lot of flags.
Honestly just the 1 man team thing alone is enough to steer clear. Consequently, I could see it as obfuscation, like perhaps there’s a bad-actor-team like a government or agency, or whatever other entity that’d benefit off a honeypot of Kodachi’s target audience.
One thing I’d really appreciate is that you mentioned how it’s basically a glorified Ubuntu w/ not-well-written anon./opsec-type scripts. Could you revise and add in what those scripts one should/would want to have running?
I plan on using Whonix/Qubes after this, I think. I’m sure a lot of it is built in…
I’ll be sure to spread your article! Its very valuable from a novice standpoint, we often learn more from what NOT to look for from whatever solution one is interested in, than what we learn from researching the right solutions. Cheers!
Dear Sir, please review mofo linux.
Thank you for this review. Now where do I sign up for your classes and I’m not masquerading under false pretences. Teach me
What’s worse, is the creator of this ‘distro’ also publishes articles on topics such as “how to get mass marketing email to the inbox”, talking about tools he created in Visual Basic to basically be a spammer. Pitty to those who use this trash expecting privacy or security.
https://www.digi77.com/getting-marketing-email-to-the-inbox/
@Everyone, Hi,
I am one of the @Support Team Members of the Linux Kodachi Distribution Operating System, The issues listed in the news article above have been fixed and this is an old news article about the Linux Kodachi Distribution Operating System. Here is a announcement made by the owner of the Linux Kodachi Distribution Operating System in the Linux Kodachi Distribution Operating System Discord Chat Server below.
”I want to take a moment to address an older audit article about Kodachi that you might have come across. The piece, titled “Kodachi Linux: A brief Security Review,” was published back in 2021?1?. I appreciate the time and effort the author put into reviewing Kodachi, as it’s through such examinations that we can identify areas for improvement and continually enhance the security of the OS.
Since the publication of this article, I’ve been tirelessly working to address the valid points raised. Many of the concerns mentioned in that audit have long been addressed and resolved. I’m proud to say that we’ve had multiple new releases since then, each one progressively addressing and rectifying the valid issues that were pointed out.
Of course, there were some points in the audit that I didn’t agree with, or that I felt were based on misunderstandings. Those I left as they were. However, I assure you that any valid bugs have been dealt with swiftly and effectively.
Security is an ongoing journey, not a destination. As the developer of Kodachi, I remain committed to continually improving its security and privacy features to serve you better. Thanks for your understanding and support”. – Owner of the Linux Kodachi Distribution Operating System.
About the news article listed here. https://bitsex.net/english/2021/kodachi-linux-is-probably-not-secure/ .
Source: Linux Kodachi Distribution Operating System Discord Chat Server
https://discord.com/channels/634355232293519362/634362597621104691/1110631132166365304
What you obviously don’t grok is that I spent a few hours on this – and found multiple glaring security problems. Your reaction when that was pointed out was to ignore the criticism.
The things I pointed out is absolutely trivial stuff. It’s not an in depth analysis. It’s not obscure things. It’s the basics. When you can’t get the basics right, and do so many stupid things, my conclusion is that I don’t trust you – ever again. Nor would I suggest anyone else should trust you. What you’ve shown is simply not convincing.
Part of security is trust – because most people don’t review the products they use.
Thank you for pointing out the initial and basic flaws of Kodachi, and for maintaining its comments section.
I checked out the Discord server linked by the poster claiming to be in Kodachi support; Ubuntu 18.04 having reached EOL almost two months ago, someone there had asked about this and was told by an admin Kodachi doesn’t need updating; and under their Discord “general” section, a week or so ago admins got into a digital shouting match when some called for proof the USA DOD was now using Kodachi to run an air force weather analysis system…as one admin alleged. In other topic conversations, I saw a liberal use of coarse language by admins and posters alike. The developer himself appears to fade back and let the posters do the talking. Still a one-party developer.
As for the OS, now 8.27, same basic issues as you first reported; Conky may now show ever-changing hwid on screen, but boot ID via dashboard section shows one and only one ID still going out on boot forward; when connected onscreen to “Kodachi VPN” only, every check at Browserleaks shows Tor exit nodes; the DNSCrypt actually works just with clearnet and is “active” on display only if “used” with Tor or vpn (checking with leak tests and comparing output IPs with a public list of DNSCrypt servers).
There’s probably nominal privacy re non-attacker tracking, but no more than most vpns basically give; as for anonymity, seems Kodachi may have all those neat apps and browsers, but the streaming boot ID is probably saying “That’s the one who used the obfuscation” at every connection. “Extreme privacy out of the box”, “Peer of Whonix, Qubes, etc” seems a bit over the top in this present situation.
To be absolutely clear – the main issue in my opinion is that these issues made it into a release. That shows a total lack of both security mindset and knowledge. My blunt assessment is that it’s impossible to trust Al Maawali again, after noting the level of incompetence so far. Especially given the initial response by him to my criticism.
This article is very deceptive.
Did the author deliberatly leave out half of the quote to mislead the reader, OR – since this article was published – did Kodachi update the “hardware ID (hash)” issue?
Check out the ENTIRE quote
“I pay a monthly rent to run the VPS nodes and provide you with a VPN service. I want to assure you that I do not collect or store any user data or information (logs) except for the hardware ID (hash) and the connected IP address (VPN IP). This information is automatically sent when your PC establishes a connection to the VPN. However, you have the option to opt in to randomize your hardware ID, ensuring increased privacy and anonymity. If you are using your own VPN or one of the commercial VPN services already integrated into the Kodachi dashboard, no hardware ID information will be sent to the server.
Firstly, insightful.
I installed this and in error did so alongside my distro of Kali Linux and now realise that was a bad bad mistake. When I tried to change the resolution from 3480 x XXXX down to something more readable it logged me out (WTF?) and sent me back to the enter password screen, despite several attempts I could NOT get back into it.
Also reading on reddit and some flames about ‘their’ enforced VPN. This distro has more red flags than a May Day parade in Red Square.
I wholeheartedly agree with the assessment that this guy (probably some amateur script kiddie) doesn’t know what he’s doing (or thinks he does) and has mackled together the distro added some bells and whistles and called it a fancy name.
I call the distro “Bullshitski” Whilst it looks good, its’ security elements have more holes than a swiss cheese. The aspect of some CPU time being taken up for bitcoin mining I read made for uncomfortable reading.
The WHOLE principle of Linux is that it is FREE aka Nada, nowt, zero, zilcho. You don’t pay for it, yet our sand dweller here charges you in CPU uptime to make money for him/them/team WTF?!
Needless to say I dropped this and deleted the ISO, I was going to run this in a VM but not now, it’s been erased permanently.
This Al-Qaeda guy needs to go back to Linux summer camp and learn it properly before releasing a distro that is a mackled together POS.
As for the Discord bit, Jesus Christ how poor. These guys should go work for North Korea’s hacking team.